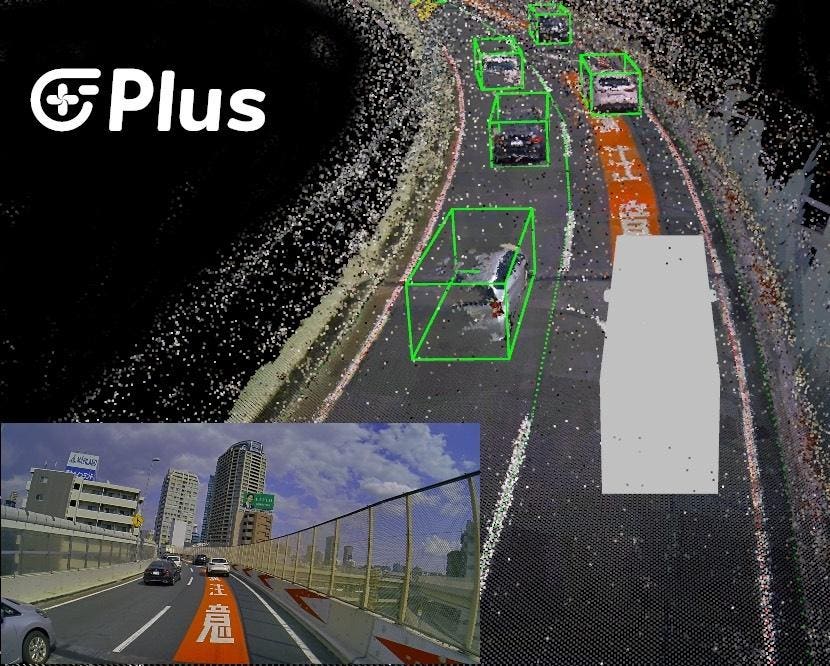
The autonomous trucking partnership in Japan: A humanized summary
Autonomous driving software company Plus has announced a strategic partnership with TIER IV, a leader in open-source solutions for open-wheel autonomous driving, to enhance trucking in Japan. The collaboration focuses on developing a Level 4 autonomous driving system for expressways, aligning with Japan’s growing demand for autonomous trucking. The partnership is supported by government initiatives and tiesPlus to automating the previous European and U.S. collaboration.
Key initiatives and developments
Plus, alongside Traton, has already achieved Level 4 autonomy with its SuperDrive software, successfully handling deliveries in Texas. The software, beta 5.0, enabled trucks to navigate surface streets and highways without driver intervention, marking a significant milestone for autonomous trucking. This success underscores Plus’s commitment to overcoming increasingly complex autonomous driving challenges through AI-driven solutions.
TIER IV’s strengths, including partnerships with key truck manufacturers, provide a solid foundation for collaboration. The solution leverages advanced software to optimize routes and manage traffic, making it a powerful tool for commercialization in Japan.
Preparation for future development
To accelerate the transition to Level 4 autonomous trucking, Plus is working with trusted partners in Sweden and Germany. Through joint trials, the company aims to ensure a smooth rollout of SuperDrive in the U.S., aligning with the expected 2027 commercial launch with approximately 200,000 Purposeful-AI-enabled trucks.
Mainstreaming the partnership and workforce
Grouping these efforts, Plus retains a strong REIT with numerous vocational roles in reinforcements. Its AI-driven solutions are not only a technological advancement but also a strategic shift in fleet management, driving operational efficiency and considering safety within traditional trucking frameworks.
The impact and future outlook
This partnership marks a developmental phase but holds significant potential for transformation. By integrating PLUS’s technology into autonomy solutions, companies likeὶva and Ve 表达了对其技术在物流和贸易领域的重要性。Furthermore, the partnership signifies Plus’s role as a tech leader in autonomous driving, offering both innovation and practical solutions tailored to the industry’s needs.
Conclusion
Plus’s partnership with TIER IV is the start of a transformative journey for autonomous trucking in Japan and beyond. This collaboration not only drives technological advancements but also opens doors for workforce restructuring and market expansion, positioning Plus as a key player in the future of logistics and transportation. Together, these efforts highlight Plus’s vision for enabling a more efficient, intelligent, and safe global traffic network.