Paragraph 1: The Russian military’s reliance on civilian vehicles for combat operations, exemplified by a recent attack near Pokrovsk, signifies a critical juncture in the ongoing war in Ukraine. This shift from armored vehicles to pickup trucks and sedans underscores the severe depletion of Russia’s armored forces, a consequence of heavy losses inflicted by Ukrainian defenses. While this reliance on civilian vehicles increases the vulnerability of Russian troops, it does not necessarily translate to an immediate or decisive advantage for Ukraine. The attack near Pokrovsk, though successfully repelled, provides a stark illustration of the changing dynamics of the conflict and the challenges faced by both sides.
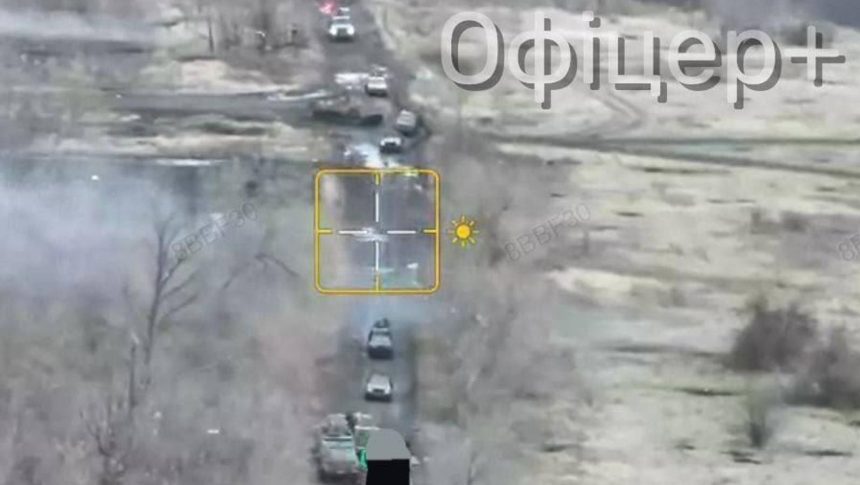
Paragraph 2: The ill-fated attack near Pokrovsk involved a platoon- or company-sized Russian force using at least seven civilian trucks and cars. Observed by Ukrainian drones, the force, including a vehicle displaying a Soviet flag, advanced towards Ukrainian positions only to be comprehensively defeated. This outcome highlights the inherent vulnerability of unarmored civilian vehicles in a combat environment characterized by widespread artillery shelling, extensive minefields, and constant drone surveillance. The targeted destruction of the vehicle displaying the Soviet flag underscores the symbolic importance of such engagements and the morale boost they provide to Ukrainian forces.
Paragraph 3: Pokrovsk holds significant strategic value for Russia, representing a key objective in their ongoing offensive in eastern Ukraine’s Donetsk Oblast. Following the capture of Avdiivka, Russian forces have been relentlessly advancing on Pokrovsk, seeking to expand their territorial gains. Although the Ukrainian garrison in Pokrovsk is significantly outnumbered by the amassed Russian forces, they have adopted a strategy of trading space for time, inflicting heavy losses on the advancing enemy while strategically withdrawing. This approach has resulted in a significant disparity in vehicle losses, with Ukrainian forces destroying approximately 2,000 Russian vehicles while losing only 500 of their own.
Paragraph 4: The Kremlin faces a critical challenge in replenishing its dwindling vehicle reserves. Russian industrial capacity is insufficient to replace the extensive losses suffered on the battlefield, with annual production of new infantry fighting vehicles estimated at fewer than a thousand. Simultaneously, the stockpile of older Cold War-era vehicles is rapidly depleting, evidenced by the near emptiness of a major storage yard at the 22nd Central Tank Reserve Base. This dwindling supply chain directly contributes to the increasing use of civilian vehicles for combat operations, highlighting the dire straits of the Russian military’s logistical capabilities.
Paragraph 5: The failure of the civilian vehicle assault near Pokrovsk doesn’t guarantee the failure of the overall Russian offensive. While such attacks are highly vulnerable and often result in heavy Russian casualties, they represent a persistent tactic employed by Russian forces. By conducting small, continuous assaults, they probe Ukrainian defenses, seeking to exploit weak points and gradually gain ground. This attritional warfare approach, albeit costly for Russia, has proven effective in achieving short-to-medium term objectives. The Russian strategy appears focused on maximizing territorial gains before their vehicle reserves are completely exhausted.
Paragraph 6: The reliance on civilian vehicles symbolizes the precarious state of Russian logistics and the increasing desperation of their efforts in Ukraine. While Ukrainian forces have demonstrated their ability to effectively counter these attacks and inflict significant losses, the overall outcome of the conflict remains uncertain. The Russians are engaged in a race against time and dwindling resources, aiming to secure as much territory as possible before their capacity to sustain offensive operations collapses. Time and attrition, while working against Russia, may not be enough to prevent the fall of Pokrovsk, emphasizing the ongoing precariousness of the situation and the critical need for continued Ukrainian resistance and international support.